- Soroco Tops Everest Group’s PEAK Matrix® Assessment - Four Years in a Row
Scout
Customer Stories
Ecosystem
Work Graph
Building Systems that Effectively and Cryptographically Protect User Privacy
- 22 July 2022
- 15 minute read
About Our Guest Speaker
Why this talk at Soroco
A work graph is a connected sequence of steps that teams execute to get work done. It is, in essence, a map of how teams execute digital work, and it lies at the intersection of people, work, and technology. Once discovered, the work graph enables teams to collaborate and work more effectively.
Watch the Talk
Powerful ideas from Ghostor and MAGE
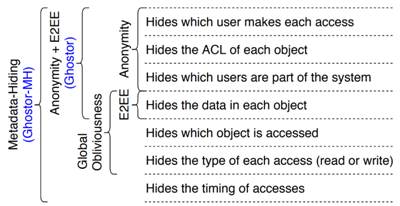
As shown above, protecting user privacy goes far beyond simply encrypting their information (i.e., the 4th layer down – hiding the data in each object). It is important to protect what users are part of the system (i.e., who has an account, who is participating), hiding timing of object accesses, and even hiding which user makes each access. For example, although the contents or even who an object in the system belongs to can be hidden, timings of access to that file or correlating those times with other information can eventually help an adversary conclude who it belongs to even if not knowing what is in it. It is first this end-to-end thinking about protecting user privacy that we found extremely valuable in system design.
Verifiable Linearizability: Second, the author’s present the importance of not just protecting the contents of information and that it is valid (e.g., via a signature), but also being able to provide guarantees that it is the most up-to-date version of the information. This is because encrypting information and signing it does not necessarily guarantee that an adversary could not simply present back an older representation of that information which could no longer be valid or missing a sensitive update to it. The author’s work in Ghostor provides a simple example of a patient system in the medical field, where an adversary could return a valid older copy of data before an individual had more recent updates to their medical records that are important to protecting their health (e.g., notes of recent allergies).
Ghostor is the author’s proposed system design that can provide the multiple layers of anonymity with variable linearizability. This incorporates a blockchain that could provide decentralized trust. That would hide user identity from even the servers that process the information, which we find is a powerful concept. The decentralized verifiability of the blockchain can also provide the verifiable linearizability of the data. Both the user and the server can validate that the information being processed is the most recent. Since there are concerns of overhead in updating the blockchain, it is proposed that a single hash that represents the entire system is updated every epoch. That provides verifiability of the entire system and its information.
Additionally, there are several properties of the system design that are important to protecting the user anonymity along with the verifiability and anonymous properties of the blockchain. For example, ensuring there are no server-visible ACLs and no server-visible user public keys as being important. There are several others that the authors present that we encourage the reader to get more details from their paper.
MAGE further builds on the principals of security and privacy by focusing on proposed improvements to Secure Computation. Secure Computation being privacy preserving technology that protects the identity of parties involved and the information being input to the cryptographic function. The only information being disclosed being the output of the function. This can allow different parties to participate in an agreed upon computation, without ever knowing the input to that function. An example being, two websites being able to use Secure Computation to collaborate and know whether a user has used the same password on their sites (which can weaken security) without knowing the actual password or the user in question.
Where MAGE’s work focuses is on the system challenges in providing Secure Computation when there is substantial overhead from the underlying cryptography. The key focuses in MAGE being providing a paging system that allows MAGE to provide highly efficient virtual memory abstractions for Secure Computation. This enables Secure Computations that potentially do not fit in memory at nearly the same speed. Doing so required the authors to carefully plan the memory access to reduce paging, in what they called memory programming. That concept being quite unique and what we believe is powerful to furthering the field of Secure Computation. Making it more scalable for functions with large memory requirements.
Additional Thoughts and Conclusions
Both Ghostor and MAGE are unique pieces of work that we believe can help further security and privacy in technology globally. As future work, we imagine a few areas to be strengthened. For example, Ghostor’s exact implementation protects user identity over the network via an implementation on top of Tor. While this can be a valid implementation, it does come with additional high latency and overhead of that network associated with it. Overall, Ghostor’s overall system design is one in which latency is traded off for additional privacy, so we wonder what improvements can be made to further extend Ghostor’s work to improve latency. The author’s of MAGE also introduce future work in their paper around how to other oblivious memory workloads (i.e., workloads whose memory access patterns are independent of the input).
We encourage our readers to watch Sam’s talk and read the author’s articles of work that was published in the conferences.
See Scout in action.
Schedule your demo now!